Common Challenges with Output Modules and How to Solve Them
Output modules play a crucial role in industrial automation systems, ensuring signals from the PLC…
FREE SHIPPING — On all orders $5000+ Dismiss
No products in the basket.

Output modules play a crucial role in industrial automation systems, ensuring signals from the PLC…

In the age of automation and Industry 4.0, the need for reliable, efficient, and safe…

Electric fryers are essential tools in commercial kitchens, known for their speed, consistency, and efficiency….

The world of transportation is undergoing a profound transformation, with automation and smart technologies leading…

In the competitive landscape of commercial refrigeration, efficiency, reliability, and precise temperature control are paramount….
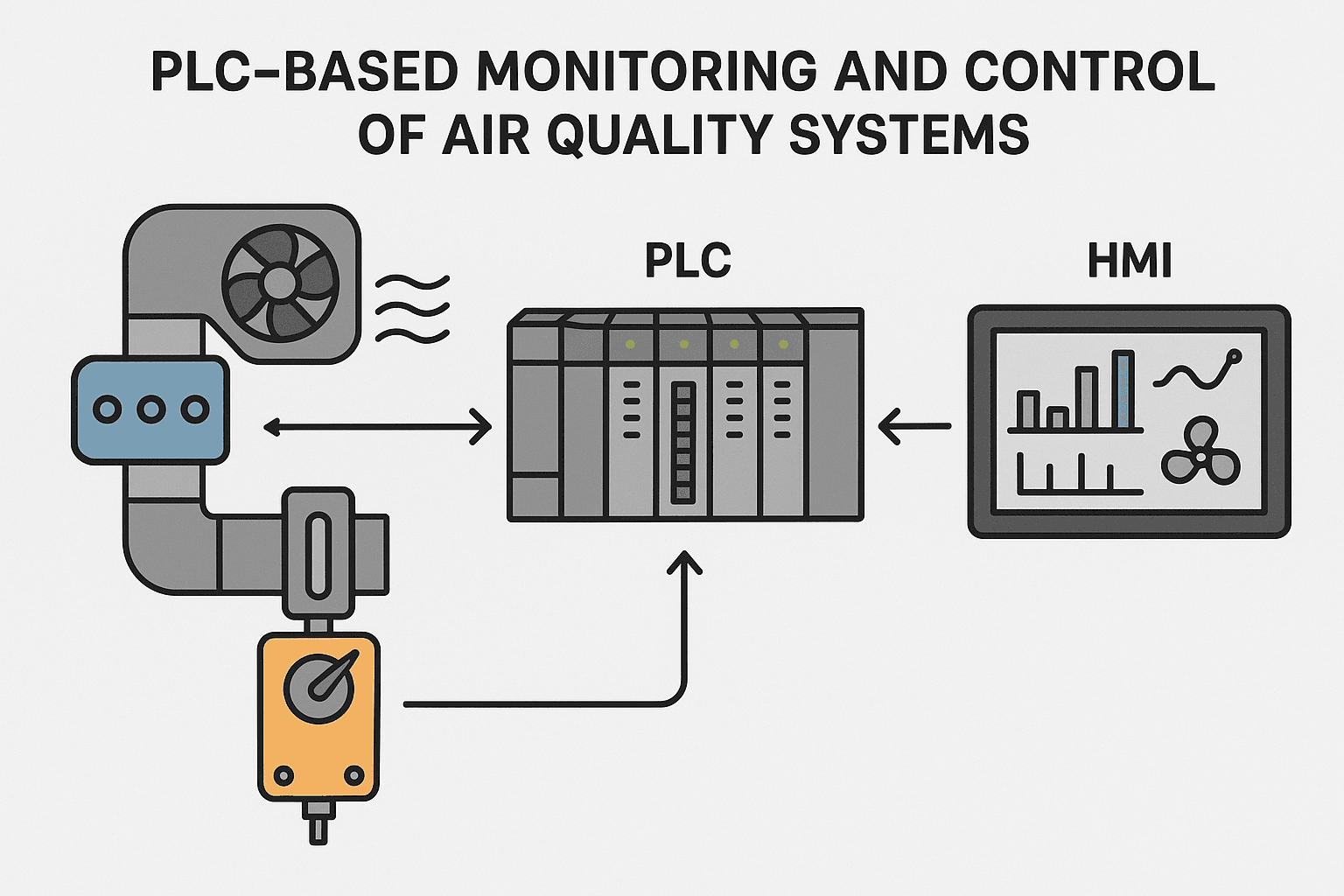
Maintaining optimal air quality in industrial, commercial, and residential environments has become a critical concern…

In moment’s period of artificial robotization, maintaining optimal temperature in artificial and marketable surroundings is…

In latest years, electric powered scooters have won full-size reputation as an eco-friendly and within…

In moment’s presto- paced and technology- driven world, the significance of robotization can not be…

In our ultramodern world, technology plays an decreasingly unnoticeable yet essential part in our diurnal…